By trx100
What is Truecrypt?
As written on the Truecrypt website, Truecrypt is – Free open-source disk encryption software for Windows 7/Vista/XP, Mac OS X, and Linux.
Where should I download it from?
http://www.truecrypt.org/downloads
So, how do I create an encrypted file container?
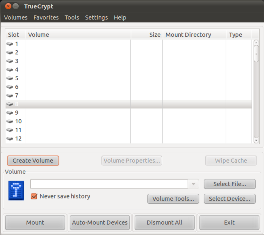
Once you have downloaded and installed the Truecrypt software, you should go ahead and open it up. You should be presented with a window which looks something like this…

- Click on the “Create Volume” button. From here, you can either create an encrypted file container on your HDD, or format an external drive or non-system partition which will then be encrypted. For the purpose of this tutorial, we’ll be creating an encrypted file container. If you wish to play around with the other option, it’s easy enough to follow and get working correctly.
- Next, the program asks you if you wish to create a “Standard Truecrypt Volume”, or a “Hidden Truecrypt Volume”. The hidden option is fantastic, as it creates a container within a container, each with different passwords. This offers deniability in case you have to reveal your password – in which case you would reveal the password to your unimportant encrypted volume. For the sake of the guide though, we’re going to select Standard TrueCrypt Volume.
- Choose your file location. Simple enough.
- Choose your encryption strength and hash algorithm. I’d leave it all default (AES, RIPEMD-160).
- Specify how much space you want to dedicate to your encrypted file container. Make it as big or as small as you need it to be.
- Choose a password. Make it s STRONG password. Read the guidelines on creating a password, as using a dictionary word isn’t good at all. Make it significantly long, and jumbled.
- Once you’ve done that, you need to decide on the type of filesystem you’re going to use. If you don’t, your filesystem won’t be able to be mounted by TrueCrypt and you wont be able to access your files. Just leave it on FAT.
- Next up is the part where you need to move your mouse around the screen in a completely random manner. Do this for as long as you want, but remember that the longer you do it, the more random and strong the encryption keys will be.
- Finally, hit the “Format” button. Your encrypted container has been created!
How do I access the container?
- Simple. When you’re on the main TrueCrypt screen, select a slot (anyone, it doesn’t matter). Then, hit the “Select File” button, browse to your encrypted container, and double click it. Once you’re brought back to the main screen, hit the “Mount” button, and put in your password.
- Double click on the newly mounted drive, and use the encrypted file to your hearts content!
Some words of wisdom by Negrophobe…
From my basic knowledge and from confirmation from others who are better in the know with programming, there is no tampering or backdoors in thre.
SERPENT 256 and TWOFISH 256 trump AES in algorithms; and truecrypt allows you to use all of them ontop of each other.
Free encryption software is the best bet for you. You’re less likely to have some programmers who are doing this for free tricking you for the government. Obviously still check the source code (if it’s closed source it’s a good bet that it’s backdoored e.g. JAP) to make sure.
With a laptop taken off the back of a van or where ever, with full encyption and random passwords on someone elses unsecure wifi; along with all flash drives encrypted and material saved onto; whilst using a VPN set up by you, or even tor; you should be relatively safe.
Keep this hidden as well and have a decoy comp and PC which you use too.
In the UK if they demand the password you can just give them the password to your work safe area whilst they can’t see any of the incriminating material, unless you give them the passphrase for that. Personally I would just stick with the 5 words instead of making their job easy.
I’d recommend reading the dr who manual (I’ll upload it when I find which flash drive it’s on)
Here’s some good links for you:
You have nothing to lose and everything to gain, if you keep your mouth shut.
Discuss
http://www.totse.info/bbs/showthread.php?t=8082